Articles

Understanding and Managing Multiple Processes for the Same Program in Windows 11
—
by
Windows 11 offers powerful tools for monitoring system performance, with Task Manager being one of…

Python Magic Methods Explained: How to Implement Dunder Methods and Operator Overloading
—
by
Custom classes in Python often feel limited compared to built-in types until you discover magic…

How to Restore and Prevent Windows Defender from Deleting Your Files
—
by
Has Windows Defender suddenly removed a file you trust, leaving you confused? Many users face…

10 Critical Challenges When Scaling Large Language Model Development
—
by
Working with multiple simultaneous Large Language Model (LLM) development sessions reveals complications that remain hidden…

How to Create a Custom Miniature-Style Depth of Field Effect in UE5 with HLSL
—
by
Creating a custom Depth of Field (DoF) effect can transform your Unreal Engine projects into…

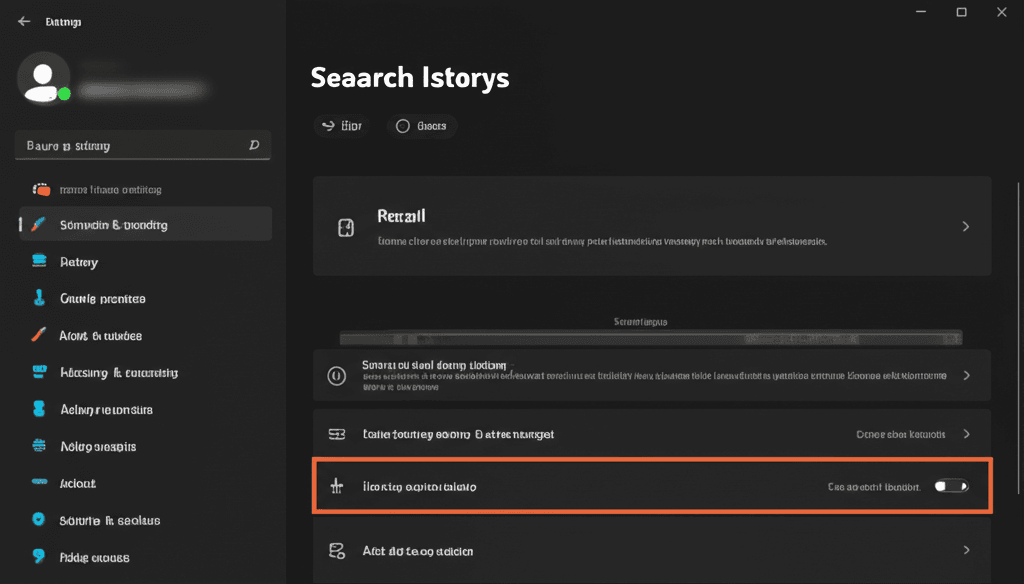
How to Clear Search History in Recall on Windows 11: Complete Privacy Guide
—
by
Windows 11’s Recall feature offers powerful snapshot-based activity tracking, but its search history retention raises…

A Complete Guide to React Testing: From Unit Tests to E2E, Snapshots, and Test Doubles
—
by
When developing with React, have you ever wondered: Where should I even start with testing?…

Waaku: Manage Multiple WhatsApp Sessions with One Dashboard
—
by
Ever tried running more than one WhatsApp Web session and realized you cannot? For developers…

Reliability by Design: Mastering Kubernetes Probes, PodDisruptionBudgets, and Topology Spread Constraints
—
by
Building reliable Kubernetes deployments requires deliberate design choices that protect your applications from disruptions while…

Massive 500% Surge in Scanning Activity Targets Palo Alto Networks Login Portals
—
by
A recent threat intelligence report has revealed a dramatic spike in scanning activity directed at…