Articles

Massive 500% Surge in Scanning Activity Targets Palo Alto Networks Login Portals
—
by
A recent threat intelligence report has revealed a dramatic spike in scanning activity directed at…

Ghost Note: The Ultimate Privacy-Focused Code Documentation Solution for Developers
—
by
Ghost Note represents a groundbreaking approach to code documentation that prioritizes privacy while enhancing developer…

How to Find Your Computer Username and Password in Windows 11
—
by
In Windows 11, your username and password are essential credentials that grant you access to…

Understanding Linear Guides in Modern Engineering: Types, Applications, and Benefits
—
by
Linear guides are fundamental components in precision engineering, enabling smooth and accurate linear motion in…

How to Fix Windows 11 Black Screen in Safe Mode: Complete Troubleshooting Guide
—
by
Experiencing a black screen in Safe Mode on Windows 11 can be frustrating and hinder…

Unlocking Collaboration with GitHub Draft Pull Requests: A Developer’s Guide
—
by
GitHub Draft Pull Requests are transforming how developers collaborate on projects, offering a streamlined way…

UTC vs GMT: Understanding the Key Differences and Best Use Cases
—
by
When discussing time zones, two terms frequently arise: UTC and GMT. While often used interchangeably…

Integrating Datadog in .NET Projects Using Serilog: A Complete Guide
—
by
In modern cloud-native and microservices architectures, applications are highly distributed, making it challenging to detect…

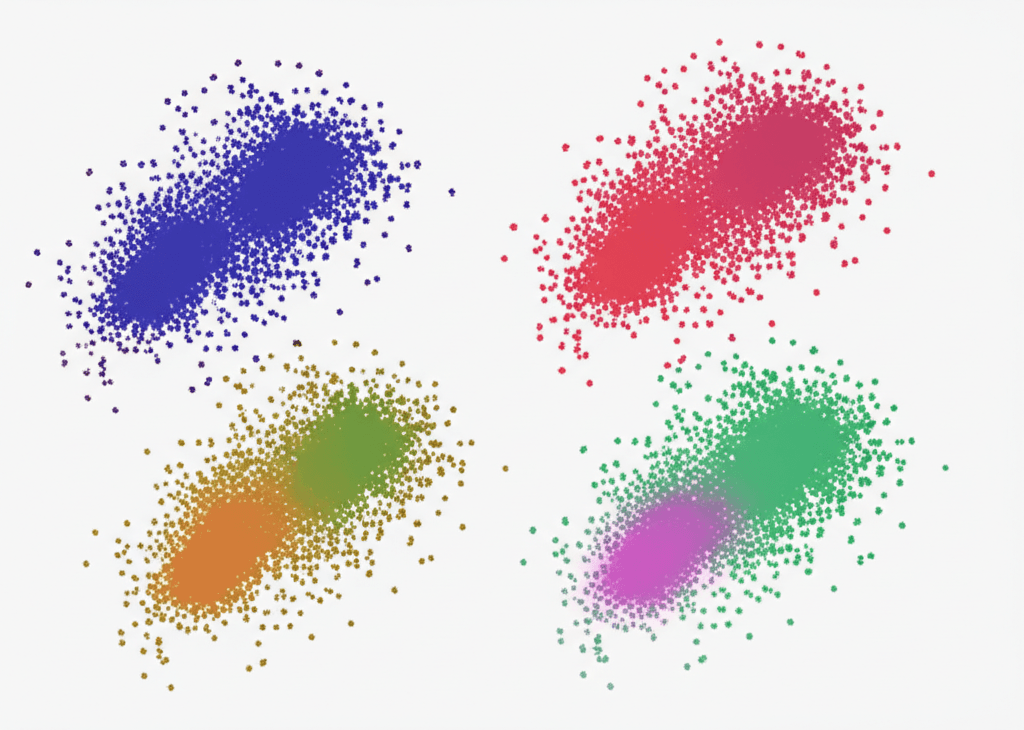
How to Achieve Consistent UMAP Clustering Results by Controlling Randomness
—
by
Creating reproducible machine learning visualizations is a common challenge, especially when using dimensionality reduction techniques…
Building a Custom CMS for Personal Blog Management: A Deep Dive into Campfire Logs CMS
—
by
Creating a custom content management system (CMS) tailored to specific needs can revolutionize how you…