Articles

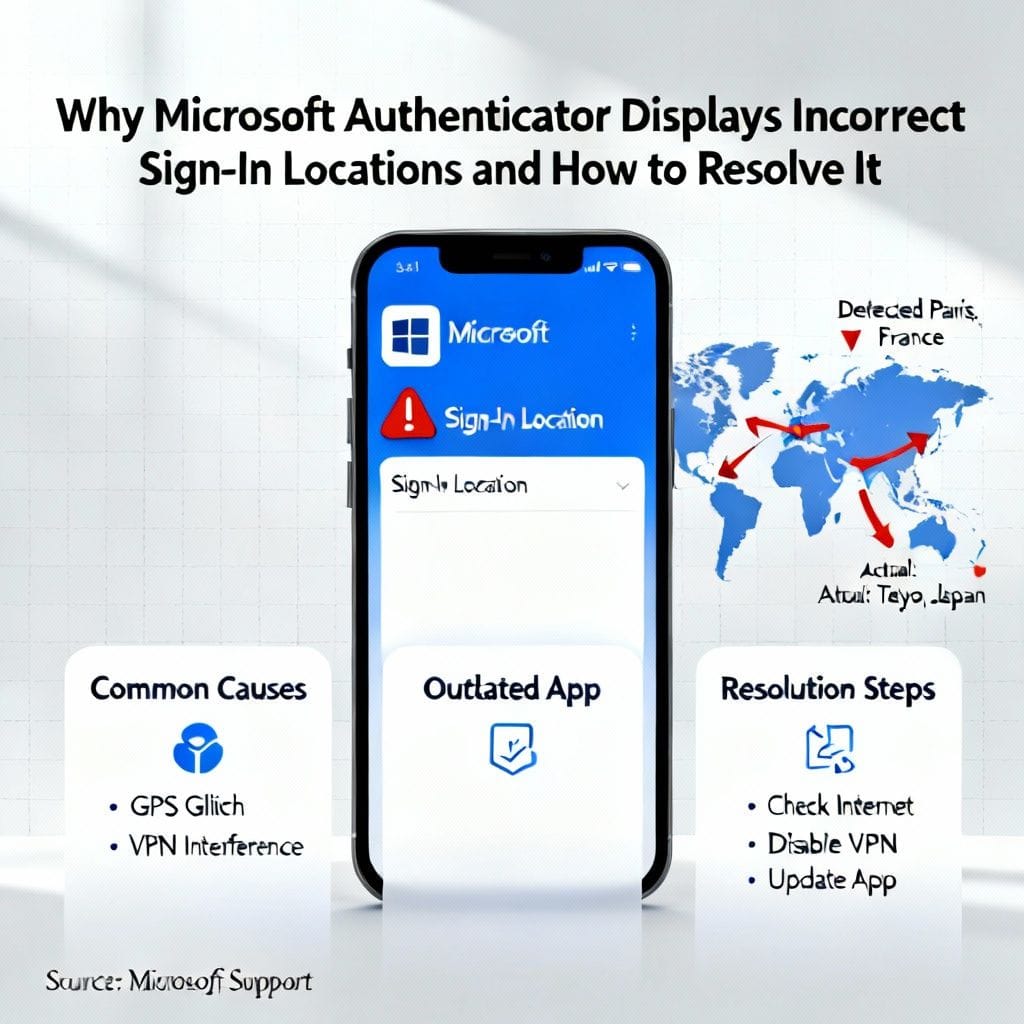
Why Microsoft Authenticator Displays Incorrect Sign-In Locations and How to Resolve It
—
by
Microsoft Authenticator is a crucial tool for securing your accounts through two-factor authentication. However, some…

Vibecoder.date: The Ultimate Dating Platform for Coders Seeking Tech-Savvy Connections
—
by
In a world where love stories often begin with a swipe, Vibecoder.date emerges as a…

Mastering Outlook Calendar Polls: A Step-by-Step Guide to Efficient Meeting Scheduling
—
by
Coordinating meeting times with multiple participants can be one of the most frustrating aspects of…

Mastering Advanced C# Smart Enums with CRTP for Optimal Performance
—
by
What Are Advanced Smart Enums in C#? Smart enums elevate traditional enums by embedding behavior…

Bitcoin Security in the Quantum Era: Breaking Down the Real Risks and Solutions
—
by
Quantum computing has evolved from abstract theories to tangible prototypes, raising urgent questions about Bitcoin’s…

Unlocking the Power of Java ORM: How easy-query Revolutionizes Subquery Handling
—
by
Subqueries are the backbone of complex database operations, yet they remain one of the most…

Step-by-Step Guide: Installing Linux Mint on VMware Workstation for Beginners
—
by
Running Linux Mint on VMware Workstation allows you to explore this popular operating system without…
How a Solo Developer Built an AI Dental Receptionist in Record Time
—
by
Most developers don’t fail due to bad ideas. They fail because integration challenges consume their…

Mastering Excel: How to Link Checkboxes to Multiple Cells for Dynamic Worksheets
—
by
Excel checkboxes are powerful tools for creating interactive spreadsheets, but many users don’t realize their…

Unlocking Google’s Latest AI Innovations: Gemini Chrome Integration, ChromeOS Updates, and Smarter Search Features
—
by
Google continues to redefine digital experiences with groundbreaking AI integrations across its ecosystem. Recent developments…